Clapping Music
Thursday night I was at a Soundstreams concert where Garry Kvistad and Russel Hartenberger, two of the four-man percussion ensemble Nexus, performed Clapping Music (1972) by Steve Reich. They walked out, stood in front of two microphones, and did it flawlessly. Fantastic. I’d heard the piece performed on radio/vinyl/CD, but never seen it done live, and never known exactly how it fitted into Reich’s phase music approach. Here’s some more about it. Knowing how it works makes it far more interesting.

As the Wikipedia entry says, “One performer claps a basic rhythm, a variation of the fundamental African bell pattern in 12/8 time, for the entirety of the piece. The other claps the same pattern, but after every 8 or 12 bars s/he shifts by one eighth note to the left. The two performers continue this until the second performer has shifted 12 eighth notes and is hence playing the pattern in unison with the first performer again (as at the beginning), some 144 bars later.”
Here’s the basic pattern:

What does it sound like? Here’s Steve Reich performing it:
That’s mind-boggling but too mysterious. You can see how much attention it would take to perform, but what are they doing?
Here’s a great animated version that makes very clear how the patterns shift:
Aha! And here’s another animated version:
Now it’s all the more clear how hard it must be to perform the piece. And to do it by juggling it, well, that would be nuts.
Or, if you’re Dame Evelyn Glennie, to perform it yourself, playing each of the two parts on each hand (this is a mix of several performances, one where she’s keeping time with her left foot):
Incredible, all of it.
See also my post about Philip Glass’s Knee Play 3, which is similarly algorithmic.
Notes from Bruce Sterling's OARN talk
Notes from Bruce Sterling’s opening talk at the Ontario Augmented Reality Network’s 2012 conference last week (5 October 2012). This is pretty much just what I took down while he was talking, and it doesn’t do justice to the talk. The third last paragraph here is a rude summary of some powerfully worded and very insightful thoughts. For another summary, see Greg J. Smith’s OARN 2012—The Shape of AR to Come.
I’ve been reading Sterling for over twenty years now. It was great to finally see him in person, and he puts on a good show. Follow his blog Beyond the Beyond to keep up with everything he’s interested in, including a lot of AR.
Showed a point cloud portrait of himself. Students had “hot-wired a Kinect” to take a 3D portrait of him. Technological underpinnings of the image: a camera tied to a Kinect with rubber bands.
Two themes for his talk:
- registration
- lash-ups with clumsy rubber bands
“Awesome new aesthetic glitch-core thing going on.”
What’s AR? “Has an augie floating around on it.”
“I’m a big fan of Ronald Azuma.” Ronald Azuma defines AR as:
- combines the real and the virtual
- interactive in real time
- registered in 3D
Showed a slide of companies involved in the AR Consortium in 2009, and ones involved now. They’re doing stuff that is sort-of kind-of registered. GPS registered, “within a couple of kilometers.” And there’s some kind of the real and the virtual, maybe just a signal, an icon, nothing too elaborate. Not a virtuality that’s so accurate it looks real. It’s interactive in real time, but not all that interactive. So all this stuff doesn’t meet the Azuma standard.
Showed the 2012 Gartner hype cycle for emerging technology. Note augmented reality heading from the peak into the trough.
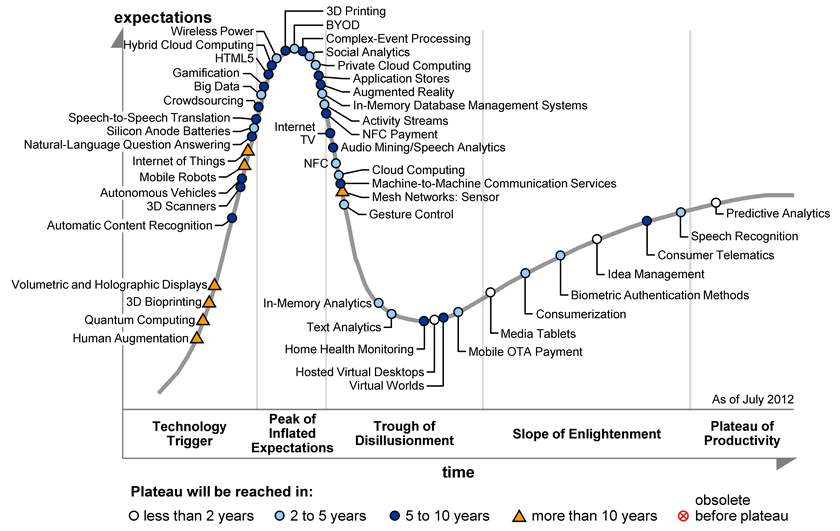
“Lovin’ the Gartner hype cycle.” “On the SLOPE TO HELL. It’s all downhill from here.” “This is where we separate the men from the boys and the women from the permanent graduate students.”
What AR companies say now: “Please stop poisoning us with inflated SF-style expectations.” We do real useful work, with services, and don’t put us in the magic box. What they started off doing, where they thought they would go, turned out to be different, but they’re still getting along, surviving, working and doing interesting stuff. They haven’t gone under yet. Layar after four years decided that “it’s about interactive paper.” Value-add to Dutch magazines. That’s what pays them.
“I"m a journalist. I never say it’s true unless two guys lie to me about it.”
Tonchidot. Ydreams, Portuguese, does installations in e.g. banks. Not what you’d have expected an AR thing to be.
Mobile software applications. Consumer visual applications. Calling it AR gets in the way.
Though the 2009 companies (on AR Consortium list) haven’t broken out to mass appeal, they’re all still around. That’s good. They’re still getting by.
“It’s all about this guy: the head-mounted display.” Purpose-built, fully registered AR devices. Showed a picture of a helmet in a NASA museum. “In my sci-fi stories it’s all about the headmounts.”
Tomi Ahonen. Guru of Layar. Ex-Nokia; mobile business analyst. “You can’t be in the mobile software industry and not read this guy.” Nokia’s failure: “It’s epic. Tolstoy would be beggared.”
Never been a mobile phone purposely built for AR. No range finders. GPS is global-scale. Phones are about SMS. That’s where the cash in.
The Cliff Effect in Mobile Phone Market Share, from Tomi Ahonen.
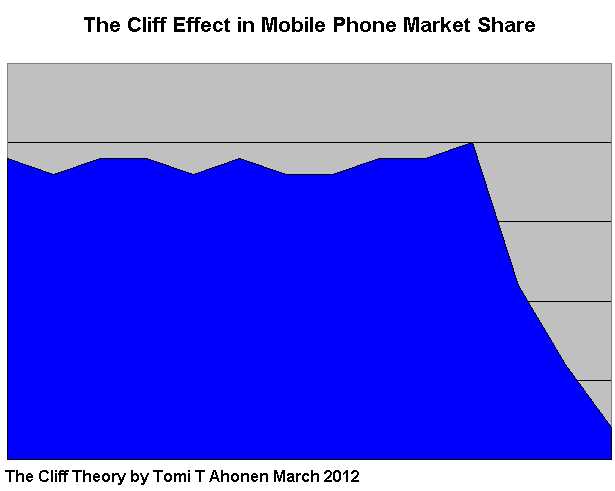
Nokia, Motorola, RIM, others, went off this cliff. There aren’t other industries where this cliff happens. They have tons of money, lots of customers, why does this happen? Replacement cycle? Dealerships change their minds about what they want to sell. Carriers are evil. The carriers cut Microsoft’s throat because they bought Skype; now no-one will carry Windows Mobile.
Layar did an augmented reality hype cycle. Layar’s doing markerless AR with image recognition. They’re installing videos in magazines.
“Mobile is everywhere and the boundaries are breaking everywhere. Society won’t wait when it comes to lashing the real and the augmented together.”
First example of AR malware. PlaceRaider. Take over guy’s cell phone, turn on camera, build 3D augmentation of his room, look around to see if there’s anything worth taking. Augmented spyware. Don’t look at all the pictures, build them into an augmentation, then use it for spying.
“It’s a coming of age when the criminal underground starts exploiting your technology. Probably got a couple of criminals in the audience today.”
Leap Motion is making the Leap. About the Leap says, “Leap represents an entirely new way to interact with your computers. It’s more accurate than a mouse, as reliable as a keyboard and more sensitive than a touchscreen. For the first time, you can control a computer in three dimensions with your natural hand and finger movements.” Gesture recognition on a millimeter scale. Couple of orders more detailed than a Kinect. (Web site says it will ship in February 2013.)
Google Glass isn’t AR, it’s a heads-up display. Doesn’t really augment. It’s an Android that isn’t handheld and responds to voice commands.
Intel’s perceptual computing. Intel wants desktop computing to keep going. Perceptual computing, voice recognition, augment the room. How do we get heavy iron on the desktop? Jazz up the space.
AR has always been piggybacking on other hardware, but now that things are breaking down, maybe AR can find a place in a gap there. Facebook, Google, Microsoft, all those things we spend our time in, they’re doomed. They’re all headed for the Ahonen cliff. Apple too—“beset with hubris.”
What does the AR victory condition look like? Submillimeter recognition. Then you’re just in a space doing things and the augments carry out your will. The ultimate AR experience is made out of AR. You’re in the space having experiences that lead you to other experiences. In a space, in a sea, where registration rules. The primary design effort is experience. What does it look like, what does it feel like, what does it do. A world where augmentation is in power. It’s not going to take power through any of the OSes or systems we have today, but that isn’t a problem … they’re not going to last. Reached a condition of volcanic instability.
There is something ahead of all this that’s hard to imagine, as hard to imagine for us as for people back in the fifties.
Final advice: Read Tomi Ahonen.
Ross Thomas and the Library of Congress
Ross Thomas’s Wikipedia entry doesn’t nearly live up to how good a writer he was. I can’t recommend him highly enough. Tony Hiss’s 1996 Atlantic article Remembering Ross Thomas is a fine introduction, and this puts it nicely:
There are actually two kinds of escape reading, and only one has to do with snuggling into a book just to take a break from your problems for a few hours. Put down a Thomas book, like a Chandler book, even on a dark night of the soul, and you’re never quite back where you were before you began reading. Something, I’ve always found, has been subtly strengthened and enriched in the meantime. It might be a sense that you can now look awful situations in the eye without dissolving. Or merely a replenished sense that good cheer can still bubble up into the world, and that there’s enough on hand for all of us to make it through another season. It’s certainly the kind of feeling that again and again makes one glad that Ross Thomas found he had to take up writing.
Ethan Iverson’s Ah, Treachery! is a full portrait and describes all his books.
Crime. Politics. Cons. Scams. Schemes. Ross Thomas knew.
I just finished The Brass Go-Between (1969), the first of his short series of books about Philip St. Ives that he wrote under the pseudonym Oliver Bleeck. St. Ives is acting as a middleman between people who stole something from a museum and the museum management who want to pay the ransom. Things go wrong. Late in the book there’s this passage, where St. Ives is in Washington and figuring out what’s going on.
When they had gone I picked up the green telephone book and looked up a number. I dialed and when it answered, I said, “What time do you close?”
“At ten o'clock,” a woman’s voice said. “The stacks close at seven forty-five.”
I said thank you and hung up and went to the window to see if Fastnaught had told the truth about the the rain. He had so I left my raincoat hanging in the closet, took the elevator down to the lobby, and flagged a cab from the sidewalk. After I was in, the driver turned and gave me a questioning look. He wanted to know where I was headed so I said, “Library of Congress, please.”
If you had enough time and enough patience, I suppose you could find out all about everything at the Library of Congress. I spent two hours in its periodical section, guided in my search by an elderly gentleman with a hearing aid who didn’t mind scurrying back and forth bearing back issues of some rather esoteric and extremely dull publications. When the periodical room closed at 5:45 I went to the main reading room and spent another hour with the bound back issues of some more tedious publications which looked as if no one had leafed through them in 20 years. When I finished at 7:30 I had acquired a sizable chunk of information and some if it might even prove useful.
It does.
If you want to try Ross Thomas, I’d recommend Briarpatch or Missionary Stew or Out on the Rim to start.
In Fear We Trust 4: LibraryBox
As I said, I’m using a slightly hacked LibraryBox to make a temporary one night only Nuit Blanche special wifi network called InFearWeTrust and web site at infearwetru.st. It’s now 4:30 in the morning and Ashley Williamson is running the lights so I can write up what I did.
I followed all the LibraryBox instructions, but I had a problem along the way. I bought the necessary TP-Link MR-3020 and installed PirateBox on it, which was easy enough … but then I couldn’t connect to the wifi network! I don’t know why. It just never responded. I set it aside to work on it later and then lost my notes about what network settings I’d used, so I think the router might be dead to me now.
I thought maybe I just had a bum one, so I got another. The same problem happened: I couldn’t connect to PirateBox! But then: I could! I can’t explain why the problem started or what stopped it. Very mysterious. However, it never came back and everything’s worked fine since then.
After installing LibraryBox I connected to its wifi network by sshing as root to 192.168.1.1. PirateBox and LibraryBox install their files into /opt/piratebox/ and it turned out there are just two files that really mattered to me: /opt/piratebox/bin/droopy and /opt/piratebox/conf/piratebox.conf.
I left the config file alone but for two things:
#HOSTNAME ... if you really want to change it, plz change:
# bin/droopy
# conf/hosts
#HOST="librarybox.lan"
HOST="infearwetru.st"
and
TEXT=""
The TEXT variable defines some stuff that shows on the LibraryBox default page, included in HTML that’s inside droopy, so I edited it right there.
droopy is a simple little Python web server (“whose sole purpose is to let others upload files to your computer” but I’m not using that). There’s a maintmpl variable that has HTML and includes some other variables. I fiddled it until it did what I needed. I kept a backup every time I did something, because every now and then I’d do something that stopped droopy from running, so I’d have to go back to the previous version and try again. Once or twice it was to do with a % sign, but once I removed a bunch of Javascript I didn’t need and that broke it. I didn’t bother to dig into it.
There are two ways to add files. The rough way is to power down the box, take out the USB drive, copy files onto it, plug it back in and turn it on. The easier way is to use scp (scp filename.jpg root@192.168.1.1:/opt/piratebox/share/).
In Fear We Trust 3
LibraryBox sitting in the window radiating an InFearWeTrust network. It’s right beside where people line up.

I’m working the lighting board. The two sheets of paper on the left are the Q (as I’m told it’s called—I’ve never worked a lighting board before, but this show has a simple lighting design).

In Fear We Trust 2
A post-rehearsal update. This is the sign people will see outside tomorrow night.

And when they connect to infearwetru.st they will see (mind you, this will change):

In Fear We Trust 1
Saturday night to Sunday morning I’m going to be part of a Nuit Blanche happening at the Arts and Letters Club. Andrew Sookrah is running a show called “In Fear We Trust,” a fourteen-minute multimedia performance with dancers, music, video (projected on the dancers) and cereal boxes. It’ll be performed about 18 times through the night, from sunset to sunrise.

My part of it is running a one-night-only Nuit-Blanche-specific temporary semi-autonomous wifi network called InFearWeTrust. It will only be accessible at the club that night. I’m running it on a TP-Link MR-3020 router with a hacked version of Jason Griffey’s LibraryBox. We’ll be feeding out music, video, pictures, drawings, schematics, ambient audio recordings and anything else we have at hand. If you’re at the club you can connect to that wifi network and get stuff that’s not on the open web. Come the dawn, the network will disappear, never to reappear.
I’ll post more about later. If you’re in Toronto and out for Nuit Blanche this Saturday night, come by. I haven’t seen a full rehearsal yet but from what I know it’s going to be good. If you’re on Twitter, use #snbto and #infearwetrust, and if you CC license a photo I’ll add it to the network.
Counting and aggregating in R
A short post about counting and aggregating in R, because I learned a couple of things while improving the work I did earlier in the year about analyzing reference desk statistics. I’ll post about that soon.
I often want to count things in data frames. For example, let’s say my antimatter equivalent Llib and I have been drinking some repetitive yet oddly priced beverages:
> bevs <- data.frame(cbind(name = c("Bill", "Llib"), drink = c("coffee", "tea", "cocoa", "water"), cost = seq(1:8)))
> bevs$cost <- as.integer(bevs$cost)
> bevs
name drink cost
1 Bill coffee 1
2 Llib tea 2
3 Bill cocoa 3
4 Llib water 4
5 Bill coffee 5
6 Llib tea 6
7 Bill cocoa 7
8 Llib water 8(Note how I specified two names and four drinks, but they repeated themselves to fill up the eight lines to equal the size of the cost sequence I specified. R does that automatically and it’s very useful.)
How many times does each name occur? That’s just basic counting, which is easy with the count function from Hadley Wickham’s excellent plyr package. Now, like a lot of R functions, the count help page is a bit intimidating.
> library(plyr)
> ?countThe help page says:
count package:plyr R Documentation
Count the number of occurences.
Description:
Equivalent to ‘as.data.frame(table(x))’, but does not include
combinations with zero counts.
Usage:
count(df, vars = NULL, wt_var = NULL)
...
Hmm! But there are examples at the bottom, and like all R documentation, you can just run then and look at what happens, which will probably explain everything. And here are more. How many times does each name occur?
> count(bevs, "name")
name freq
1 Bill 4
2 Llib 4How many times did each person drink each drink? To say you want to tally things up by more than one column use the c function to combine things into a vector:
> count(bevs, c("name", "drink"))
name drink freq
1 Bill cocoa 2
2 Bill coffee 2
3 Llib tea 2
4 Llib water 2It’s all pretty easy. Just tell count which data frame you’re using, then which columns you want to tally by, and it does the counting very quickly and efficiently.
How much did I spend in total? How much did I spend on each drink? aggregate does the job for this kind of figuring.
aggregate package:stats R Documentation
Compute Summary Statistics of Data Subsets
Description:
Splits the data into subsets, computes summary statistics for
each, and returns the result in a convenient form.
Again, there are good examples at the end of the help file. But for my example, first let’s see how much Llib and I have spent on each kind of drink:
> aggregate(cost ~ name + drink, data = bevs, sum)
name drink cost
1 Bill cocoa 10
2 Bill coffee 6
3 Llib tea 8
4 Llib water 12That command says “I want to apply the sum function to the cost column while aggregating rows based on unique values in the name and drink columns.”
How much did we each spend total? Forgot about aggregating by drink, and just aggregate by name:
> aggregate(cost ~ name, data = bevs, sum)
name cost
1 Bill 16
2 Llib 20What was the mean price we paid? Change sum to mean:
> aggregate(cost ~ name, data = bevs, mean)
name cost
1 Bill 4
2 Llib 5 Miskatonic University Press
Miskatonic University Press