Here’s an update to my post a month ago about the Firefox extensions I use on my laptop to increase privacy. I’m no expert, and it may do little or nothing against spy agencies, but it does confuse corporate tracking, which is also important. One key point, which does defend against spy agencies: use Tor more (but watch out). Every grain of sand we each throw in the gears is a help.
Remove Chromium
First, though, yesterday I deleted Chromium, the purportedly free and open browser that Google extends to make Chrome, its proprietary browser. I had used it as the only browser for using my Google accounts (which are purely for work) and for other web sites that had unreasonable demands for cookies and Javascript but that I had to use (such as for buying a ticket to a concert). Then I saw Rick Falkvinge’s Google Chrome listening in to your room shows the importance of privacy defense in depth, which reports that the browser was secretly downloading a binary that would let it listen for “ok google” in order to trigger searches.
The browser required a setting to be turned on to actually start listening, Google says, but nevertheless, without my knowing it, a blob of unknown code had been installed on my computer that could listen to my microphone. The links in Falkvinge’s piece are worth following to what developers thought of this and how Google handled it. The Guardian picked up the story with Google eavesdropping tool installed on computers without permission.
My response:
$ sudo apt-get purge chromium-browserOf course, I am walking around with a perfectly constructed and highly sophisticated monitoring device in my pocket which must have its microphone turned on—because it’s my phone—but that’s another issue.
I’m not sure what browser I’ll now use for Google access.
Extensions I use
Now, the extensions. I deleted Adblock Plus and now use uBlock, thanks to a recommendation on Twitter. It’s under the GPL v3 and completely free and open, and isn’t, in effect, a protection racket, as described in Both AdBlock Plus and the media are worried about Safari’s upcoming features.
AdBlock Plus needs to work well for its parent company to make money. Not from its users, of course, but from the companies that want to pay the company to make sure their advertisements aren’t blasted into oblivion by the extension.
On my phone I’m still seeing lots of ads (and hence being tracked) but that’s another issue too.
I also installed NoScript, which I should have done a long time ago. It blocks Javascript (and some other things) on sites unless I enable it where I want it to run. It comes with a whitelist, but it’s editable.
This is my updated list of privacy extensions, with their licenses (MPL == Mozilla Public License, GPL == GNU Public License) and links to source if public:
- Better Privacy (“BetterPrivacy is freeware; Non-commercial use and distribution only!”, no source)
- CanvasBlocker (MPL, https://github.com/kkapsner/CanvasBlocker)
- Cookie Monster (MPL, no source)
- Disconnect (GPL, for-profit company, https://github.com/disconnectme/disconnect)
- HTTPS Everywhere (GPL, https://github.com/EFForg/https-everywhere)
- NoScript (GPL, https://github.com/avian2/noscript)
- Privacy Badger (GPL, https://github.com/EFForg/privacybadgerfirefox)
- uBlock (GPL, https://github.com/chrisaljoudi/ublock)
Also:
Check in on Lightbeam every few days to see a nice visualization of how your information is being passed from one site to another. It’s incredible.
Blocking referrers
None of those do anything with the HTTP referer header, so I looked into how to handle that myself. Opening the (pseudo-)URL about:config in Firefox and searching for referer (an aged misspelling) showed this:
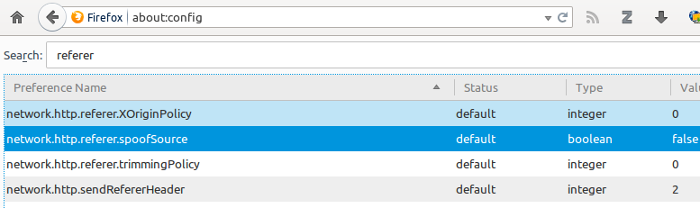
Finding the details of these is strangely difficult on the Mozilla Firefox site, but Improve online privacy by controlling referrer information documents them.
network.http.referer.XOriginPolicy
- 0: always send referrer (default).
- 1: only send if base domains match.
- 2: only send if hosts match.
I set this to 1.
network.http.referer.spoofSource
- false: send the referrer (default).
- true: spoof the referrer and instead use the target URI
I set this to true.
network.http.referer.trimmingPolicy
- 0: send full URI (default)
- 1: send scheme, host, port and path
- 2: send scheme, host and port
I set this to 2.
network.http.sendRefererHeader
-
- never send the referring URL
-
- send when following a link
-
- send when following a link or loading an image (default)
I set this to 1.
This may stop some sites from working. I’ll wait and see.
Server-side
Eric Hellman’s Protect reader privacy with referrer meta tags told me about the new referrer (finally properly spelled) meta tag in HTML 5, which allows a site owner to suggest to a browser what referrer information it should pass on to a linked site. You’re viewing this over HTTPS, so this shouldn’t matter when linking to a non-secure HTTP site: 15.1.3 Encoding Sensitive Information in URI’s in RFC 2616 says, “Clients SHOULD NOT include a Referer header field in a (non-secure) HTTP request if the referring page was transferred with a secure protocol.” However, my URL would be passed on to HTTPS sites. To prevent this, I added this to my page template:
<meta name="referrer" content="origin-when-cross-origin" />
This means that links leading off my site should pass on that the browser came from https://www.miskatonic.org/, without giving the particular page, but links staying inside my site will pass the full referring URL.
Use Tor more
I’m using Tor more. I try to use it for as much regular anonymous browsing as I can: just reading the newspapers or looking at blogs or checking something on Wikipedia or any other normal behaviour. Using Tor like this has two wide advantages: it increases the overall traffic on the network, which helps confuse what everyone else is doing, and it means that more Tor traffic hits regular web sites, which also helps confuse what everyone else is doing. The more people that use it, the better for everyone.
It has its faults. It shows ads! Here’s what the Toronto Star home page looks like right now in Tor:
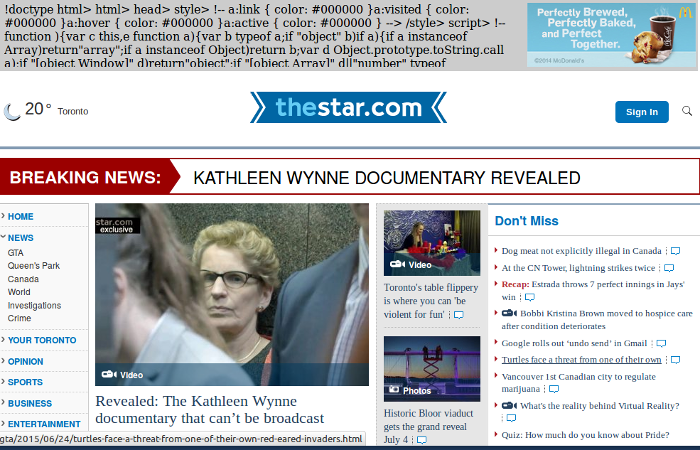
Not only do I see the ad at the top, which uBlock prevents, it’s messed up and ugly. But I don’t mind.
Using Tor (or ssh) means that you become a permanent target of the security agencies and everything you do will be logged and analyzed, so know what you’re doing.
Still, every grain of sand we each throw in the gears is a help.
 Miskatonic University Press
Miskatonic University Press